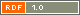
A while ago I have bought a Hi3518 based camera module from the Aliexpress.
It is called BLK18E-0712C-38X38_S (V1.01)
Some initial findings:
- No DHCP is set. Static IP at 192.168.1.10
- Default username for HTTP and RSTP is admin with blank password.
- HTTP interface lang is set to chinese atm. I have no idea where to change this.
- Streaming is done through RSTP on the following URL: rtsp://192.168.1.10:554/user=admin&password=&channel=1&stream=0.sdp?real_stream--rtp-caching=100
(Firefox did not have a plugin for this on Ubuntu, but VLC plays the stream well.)
- I have tried several telnet passwords which is out in the wild root+(juantech, klv123) but neither let me in.
NMAP log shows nothing more intresting (port 8899 IMHO for onvif):
PORT STATE SERVICE VERSION
23/tcp open telnet Busybox telnetd
80/tcp open tcpwrapped
|_http-favicon: Unknown favicon MD5: EC9D1C872C50DD7DA7D826D9C85FC158
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
|_http-title: NETSurveillance WEB
554/tcp open rtsp?
| rtsp-methods:
|_ OPTIONS, DESCRIBE, SETUP, TEARDOWN, GET_PARAMETER, PLAY, PAUSE
8899/tcp open soap gSOAP soap 2.7
Bonus:
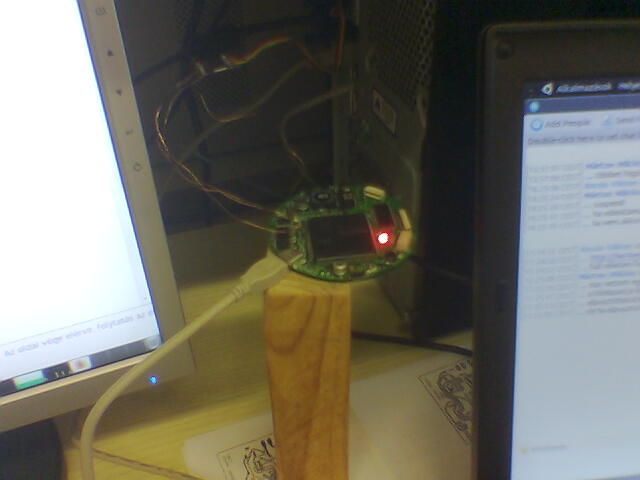
I have managed to find the UART on the device:
Uboot output:
U-Boot 2010.06-svn (Jan 04 2015 - 13:37:41)
DRAM: 256 MiB
Check spi flash controller v350... Found
Spi(cs1) ID: 0xC2 0x20 0x17 0xC2 0x20 0x17
Spi(cs1): Block:64KB Chip:8MB Name:"MX25L6406E"
envcrc 0xc96922ac
ENV_SIZE = 0xfffc
In: serial
Out: serial
Err: serial
Press Ctrl+C to stop autoboot
hisilicon # <INTERRUPT>
hisilicon # <INTERRUPT>
hisilicon # <INTERRUPT>
hisilicon # <INTERRUPT>
hisilicon # help
? - alias for 'help'
base - print or set address offset
boot - boot default, i.e., run 'bootcmd'
bootd - boot default, i.e., run 'bootcmd'
bootm - boot application image from memory
bootp - boot image via network using BOOTP/TFTP protocol
cmp - memory compare
cp - memory copy
crc32 - checksum calculation
fload - fload - load binary file from a filesystem image for system boot
flwrite - SPI flash sub-system
getinfo - print hardware information
go - start application at address 'addr'
help - print command description/usage
lip - lip - set local ip address but not save to flash
loadb - load binary file over serial line (kermit mode)
loady - load binary file over serial line (ymodem mode)
loop - infinite loop on address range
mac - mac - set mac address and save to flash
md - memory display
mii - MII utility commands
mm - memory modify (auto-incrementing address)
mtest - simple RAM read/write test
mw - memory write (fill)
nm - memory modify (constant address)
ping - send ICMP ECHO_REQUEST to network host
printenv- print environment variables
rarpboot- boot image via network using RARP/TFTP protocol
reset - Perform RESET of the CPU
run - run commands in an environment variable
saveenv - save environment variables to persistent storage
setenv - set environment variables
sf - SPI flash sub-system
sip - sip - set server ip address but not save to flash
tftp - tftp - download or upload image via network using TFTP protocol
version - print monitor version